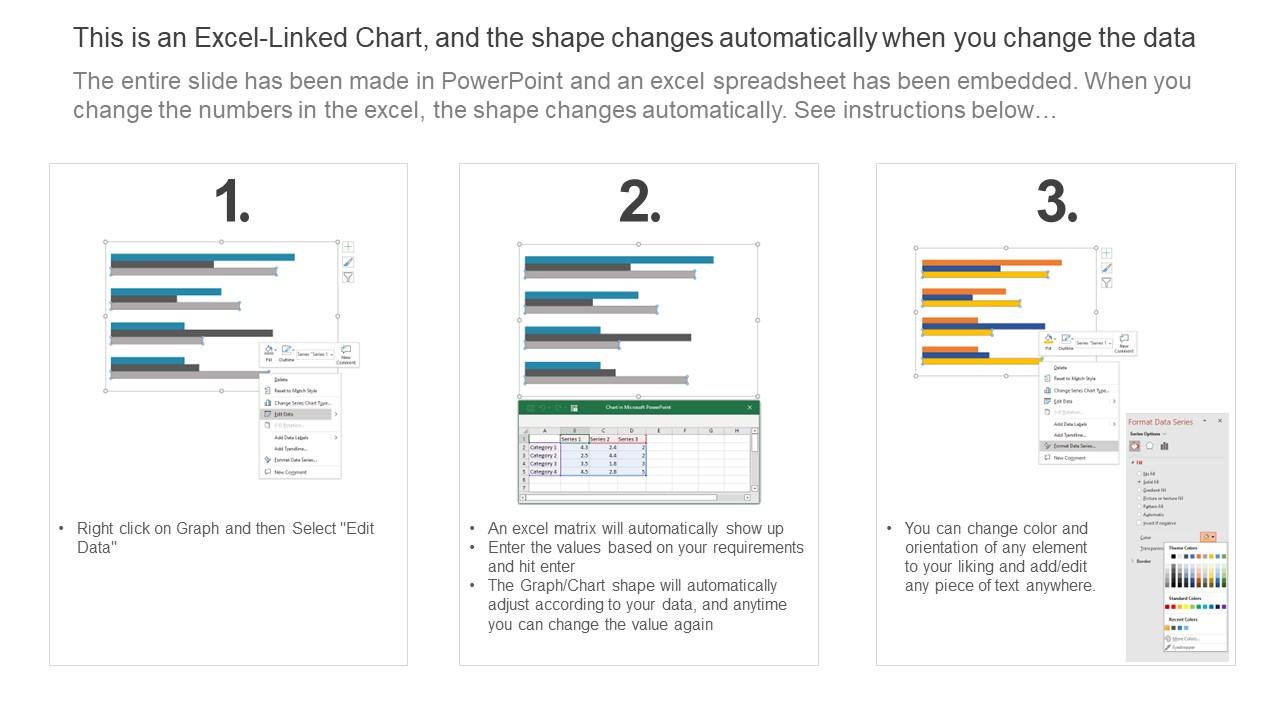
Last update images today Top 10 Cyber Attack Maps To See - Top Cyber Attack Maps Heat Map Cyber Security
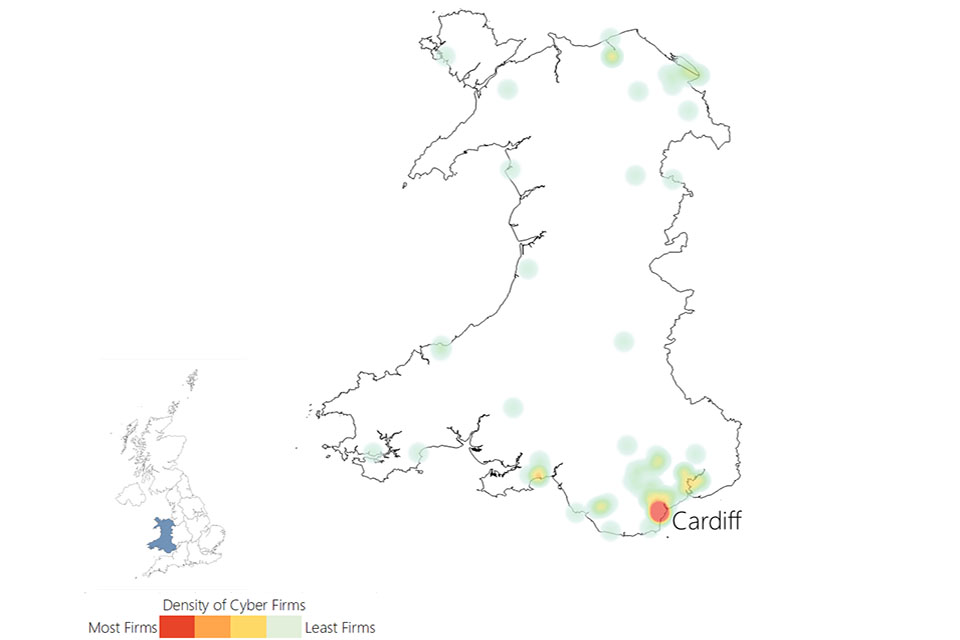
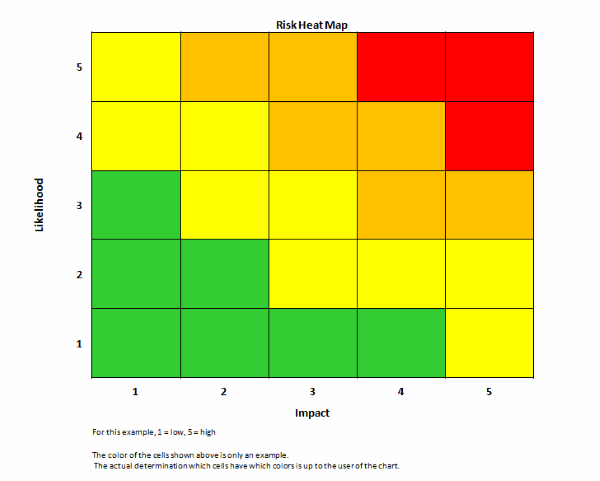
US National Cybersecurity Strategy - JfNWSd8pB3k6aSjJHpXW3B3GBTu2C3JkPJEdf4WXVeU.JPGCyber security sectoral analysis - Wales 960 X 640 BRN Fundamentals SwingTradeBot com - Android Chrome 192x192 Why Understanding RISK is Central - Risk%20Heat%20Map%201 Saturar prosperidad Inspector fortinet - Fortinet Threat Map Heat Map Template - Risk Heat Map Awz Ventures Inc Tech Details - Bizjvoijpdbmhff2zybfLogiq Consulting Tech Details - Fkx1ckh3vohbeswqfsco
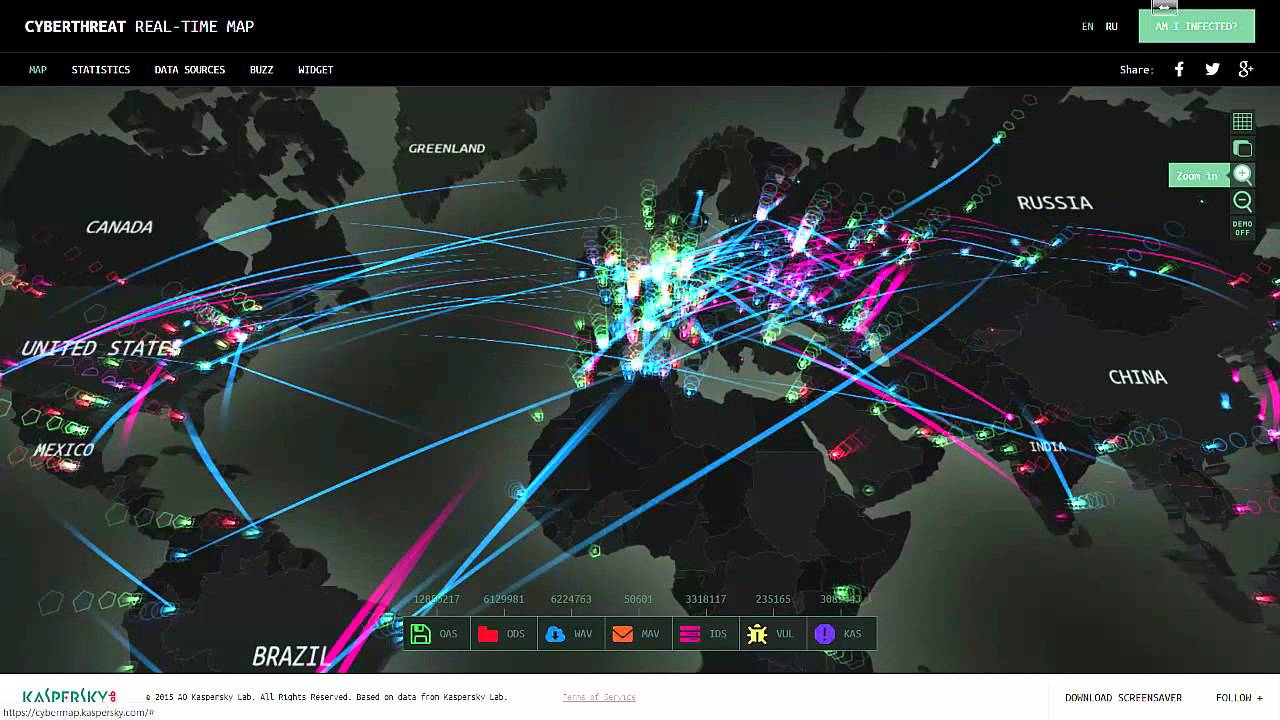
Cyber Security Padlock and Chain - Cyber Security Padlock Chain Against Pulsating Circles Over World Map Blue Background Computer Technology Concept 310886029 What is a Risk Heat Map Benefits - Risk Heat Map Trimmed Cybersecurity capability and Risk - Heat Map GreyCastle Security Tech Details - Susdt8s4i4pcq3njrlzl ComplyXpert AI Compliance Management - Pexels Kampus 8204353 Scaled What is a Heat Map in Cyber Security - Canva MADmwAd Jfw Who s Attacking Whom Realtime - Fireeyemap Top 15 Live Cyber Attack Maps for - Kaspersky Map
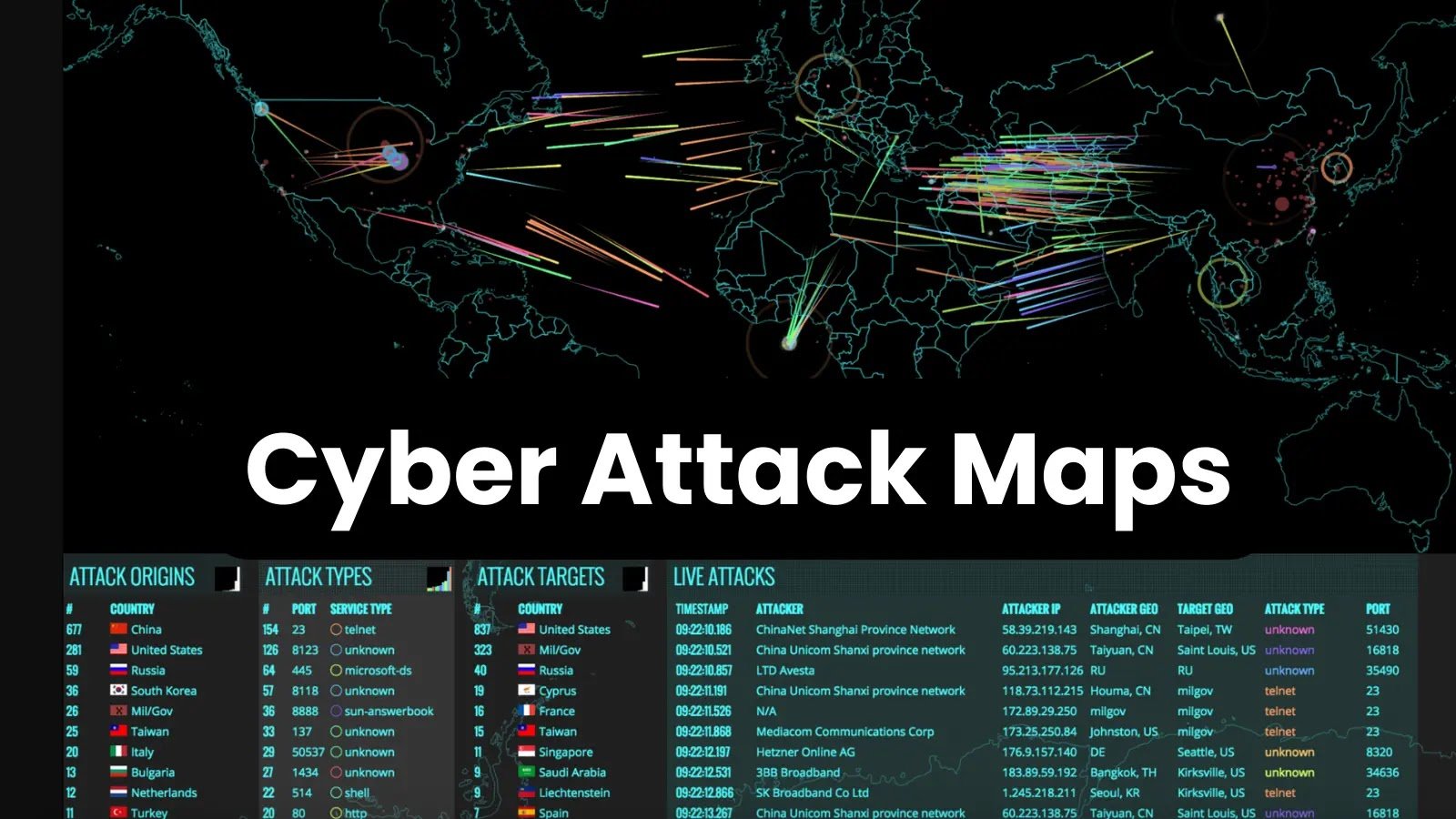
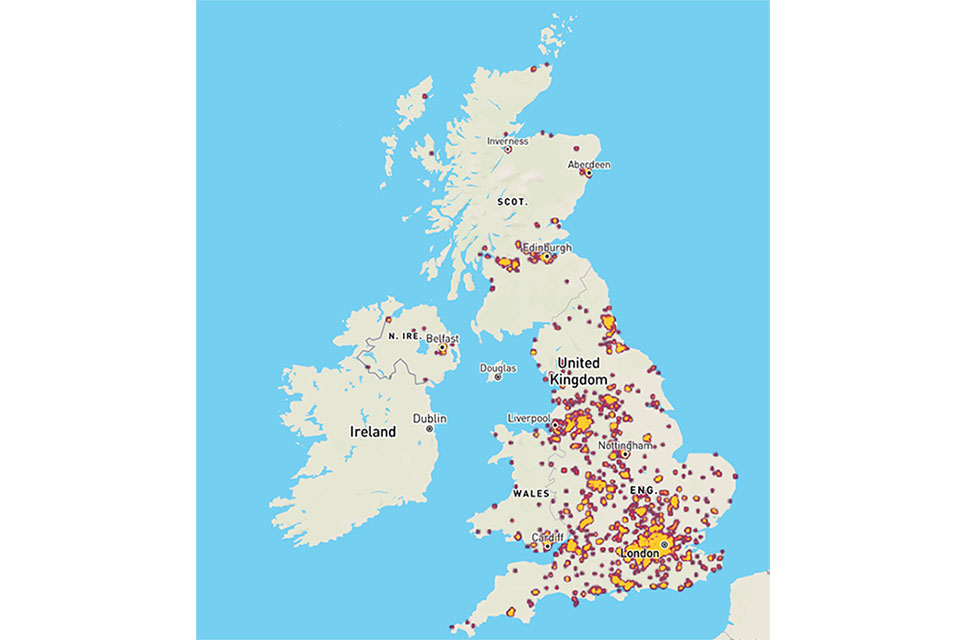
7 free cyber threat maps showing - Cyber Threat Maps 650 Top 15 Live Cyber Attack Maps for - Fireeye Map Cyber security sectoral analysis - 3.3 960 X 640 Cybersecurity through information - Career%20Map%20for%20Infromation%20Security Why a Global Security Alliance - Screenshot 2025 07 06 At 22.24.23 The Risk Assessment Threat Matrix - Heat Map 22 00 Wireless Heat Maps Cybersecurity - 1200w630hTop 8 Cyber Threat Maps To Track - Best Threat Maps
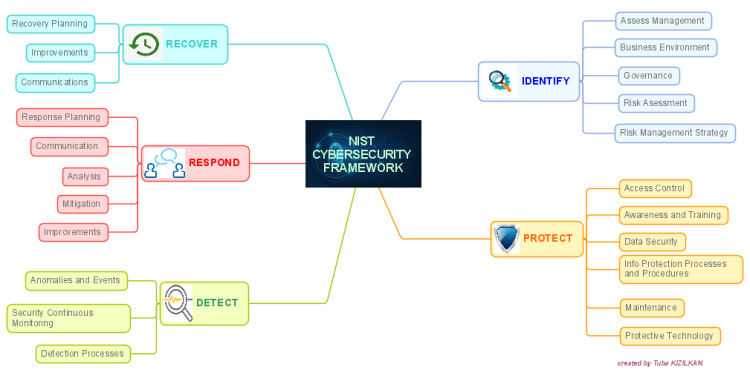
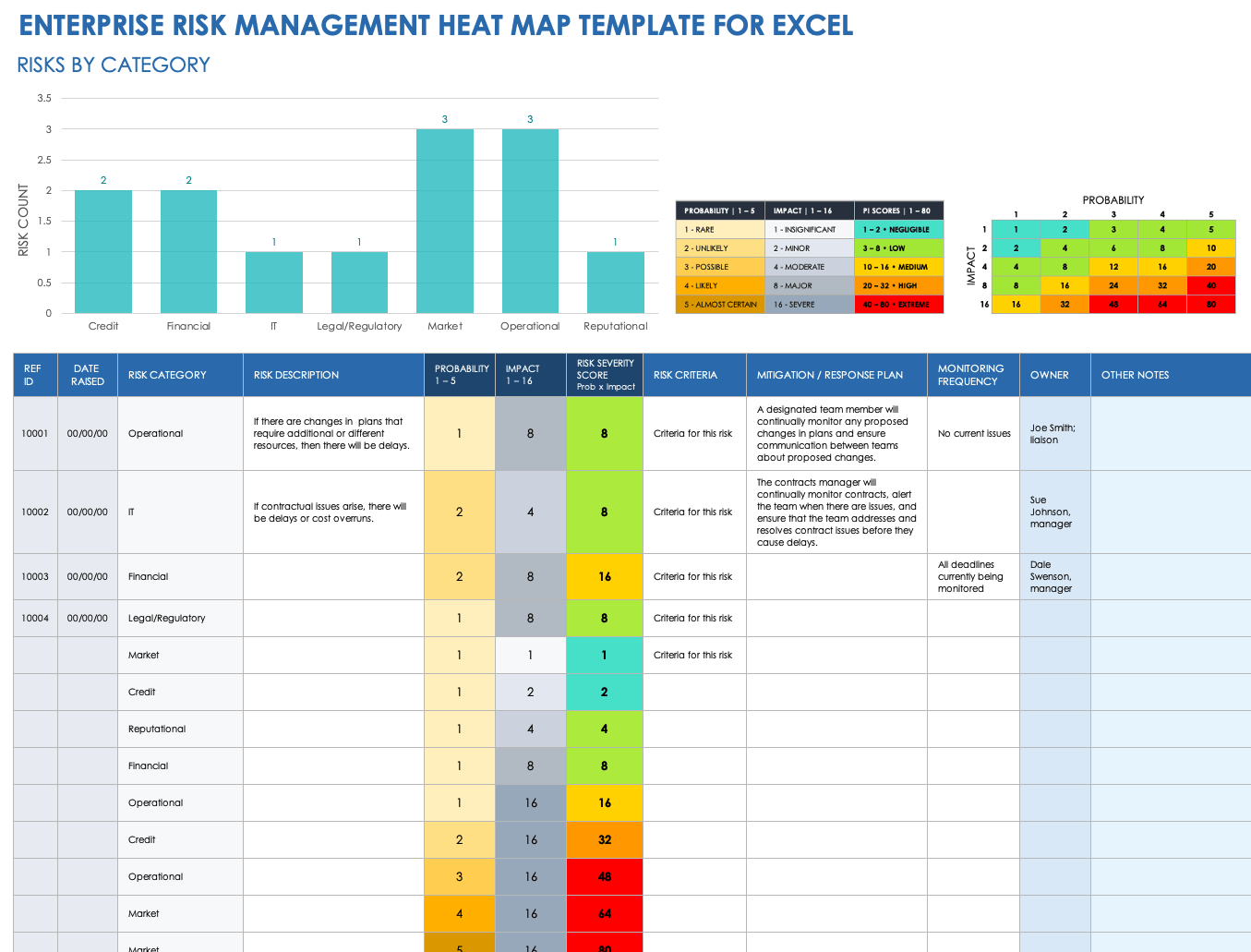
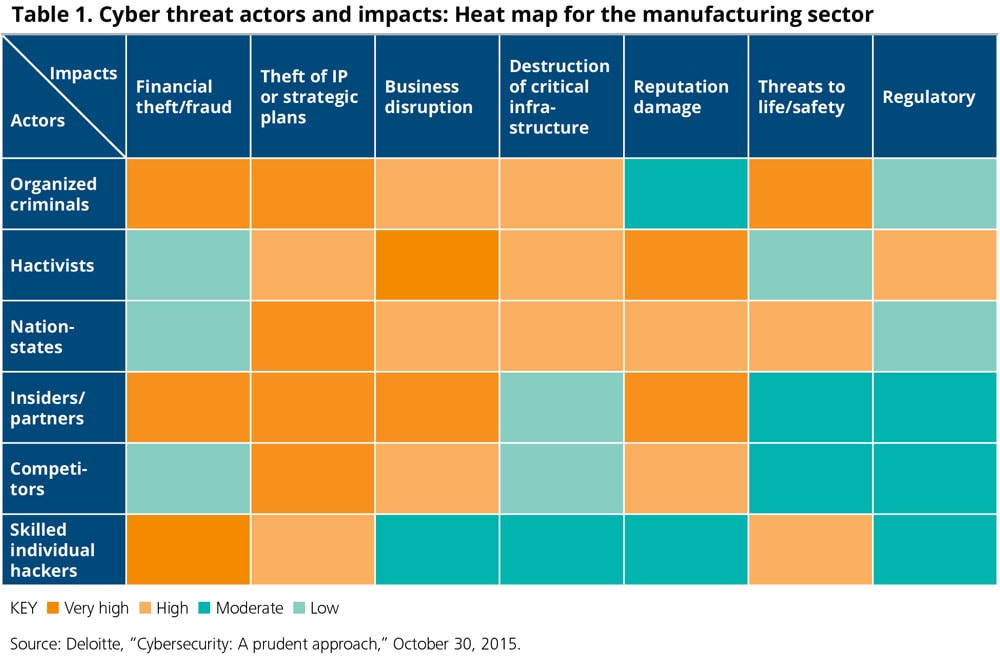
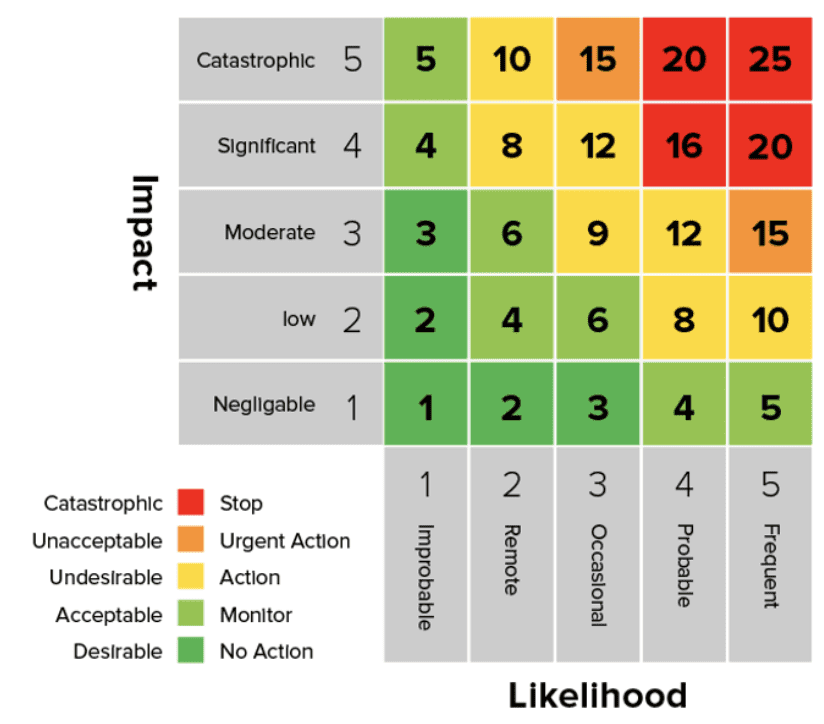
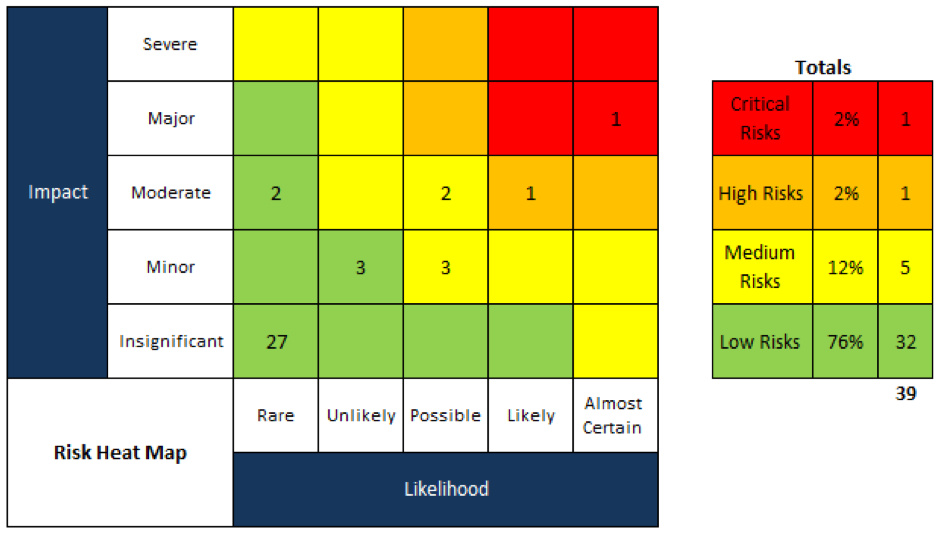
Cybersecurity Risk Assessment Program - Cybersecurity Risk Assessment Program Mapping Of Multiple Cyber Attacks Using Risk Heat Map Slide01 NIST CYBERSECURITY FRAMEWORK iMindMap - 4GZYZCPf NIST CYBERSECURITY FRAMEWORK Mind Map Additive manufacturing and cyber - 3D Opportunity Risk Management Table1 Nist Framework Heat Map - Cybersecurity Framework Comparison Tip of the Week How to Turn Your - Cyberessentials 1024x864 Top 10 Risk Heat Map Templates - Enterprise Risk Assessment Heat Map Luminys - Luminys NSSF UGANDA Integrated Report - Heat Map 2
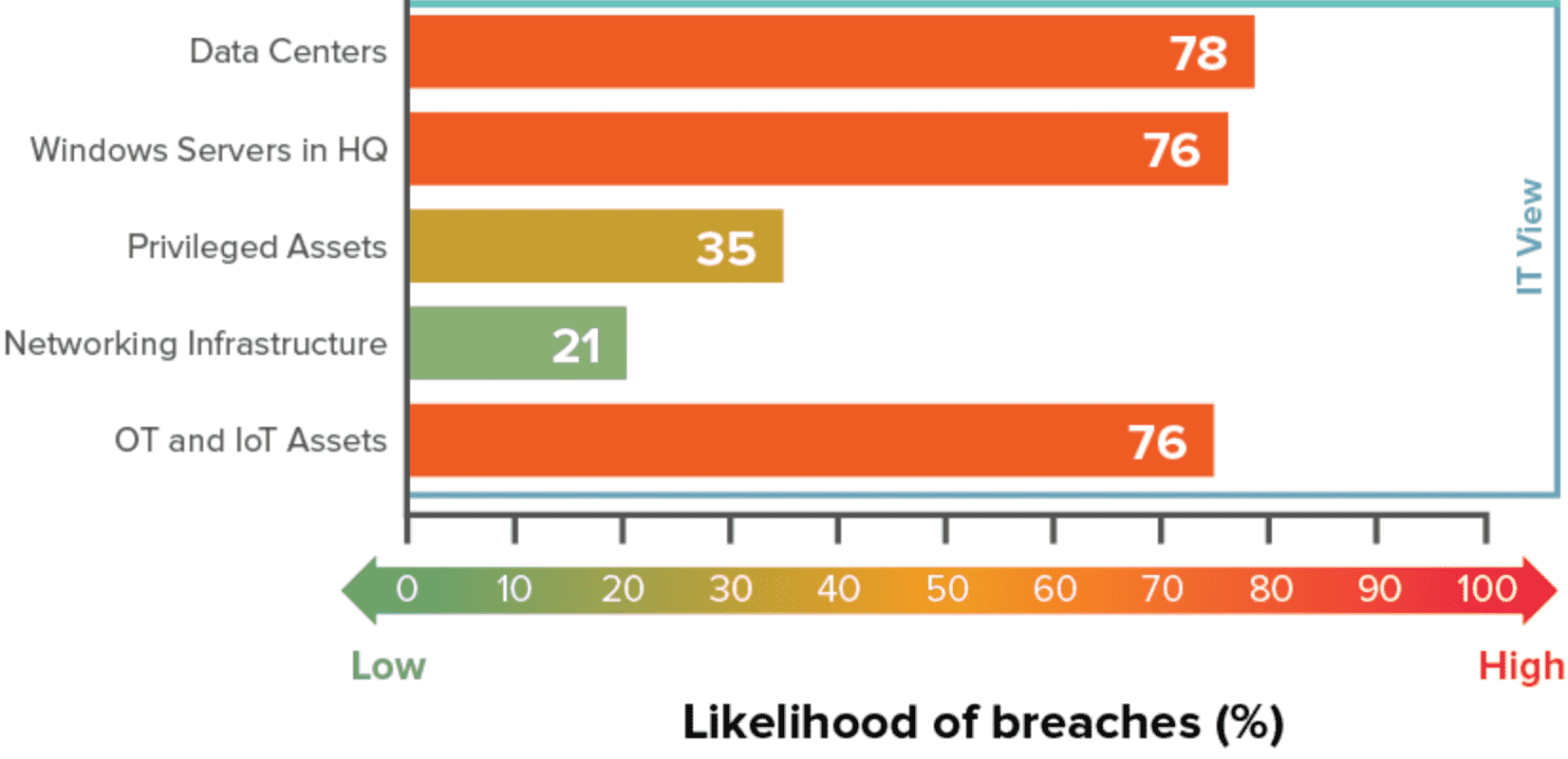
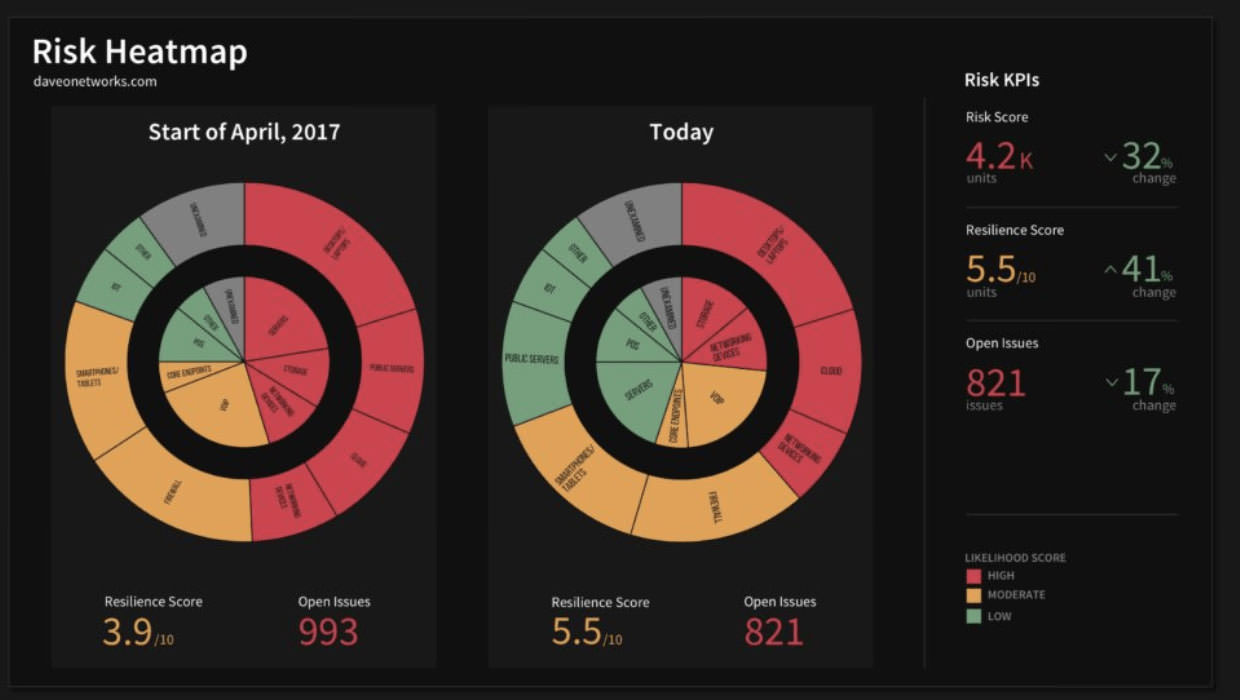
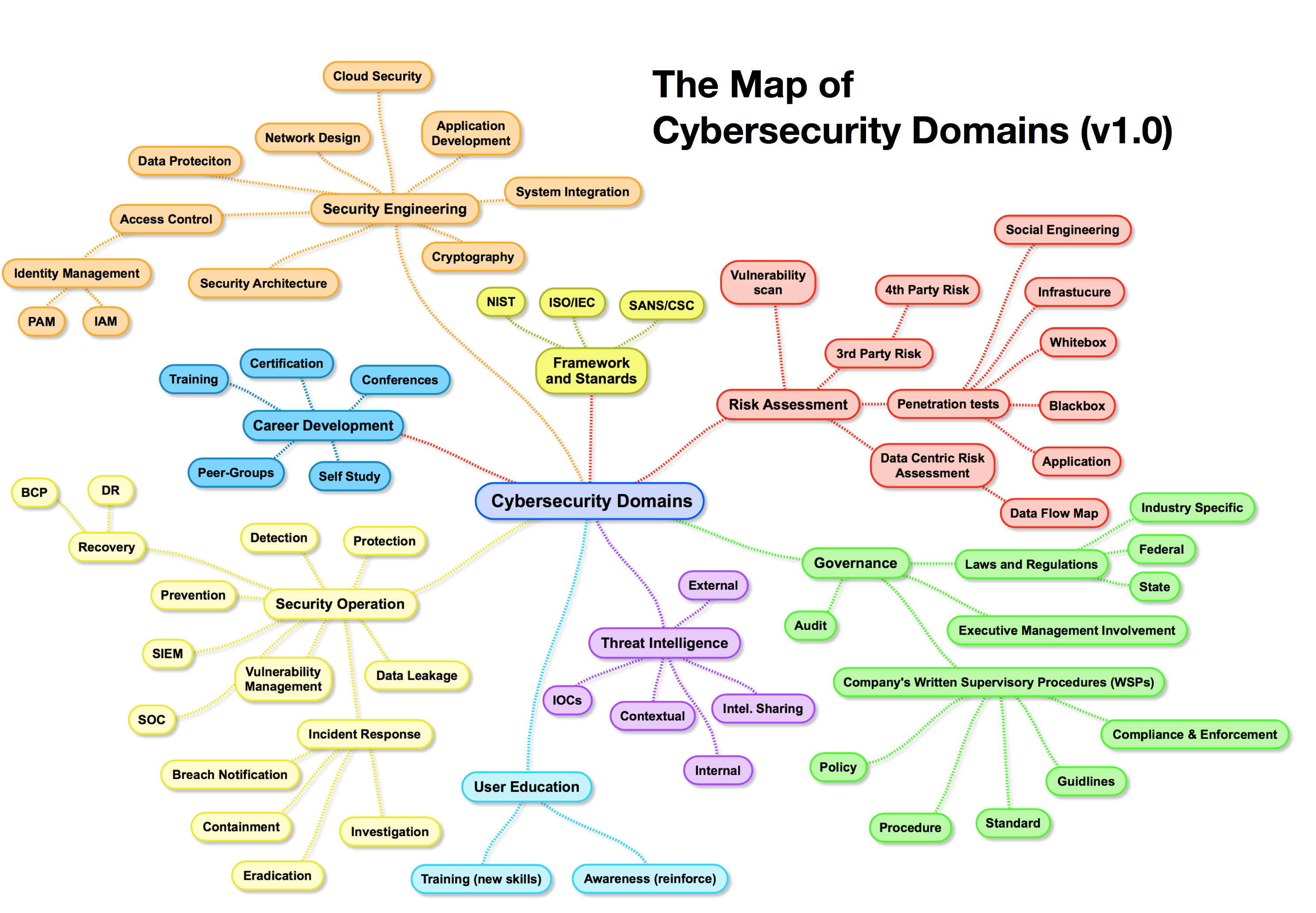
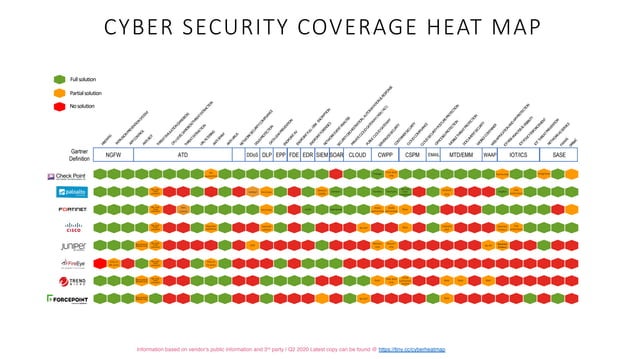
Heat advisory in effect in MA through - 6d11edae318f01440f55976e1733fadbCyber threat heat map feryinside - Cyber Attack Maps Are A Trove Of Information 468629 3 Excel Heat Map Template - IC Enterprise Risk Management Heat Map Template Cyber Threats amp Security Facts - Unika Infocom Cyber Threat Map 1 4 Steps to a Smarter Risk Heat - Heat Map 1 Cyber Security Domains - StationX Cyber Security Domains V1.1 2 Groslive Blog - Heat Map It View Cyber Security Coverage heat map - Cyber Security Coverage Heat Map 1 638
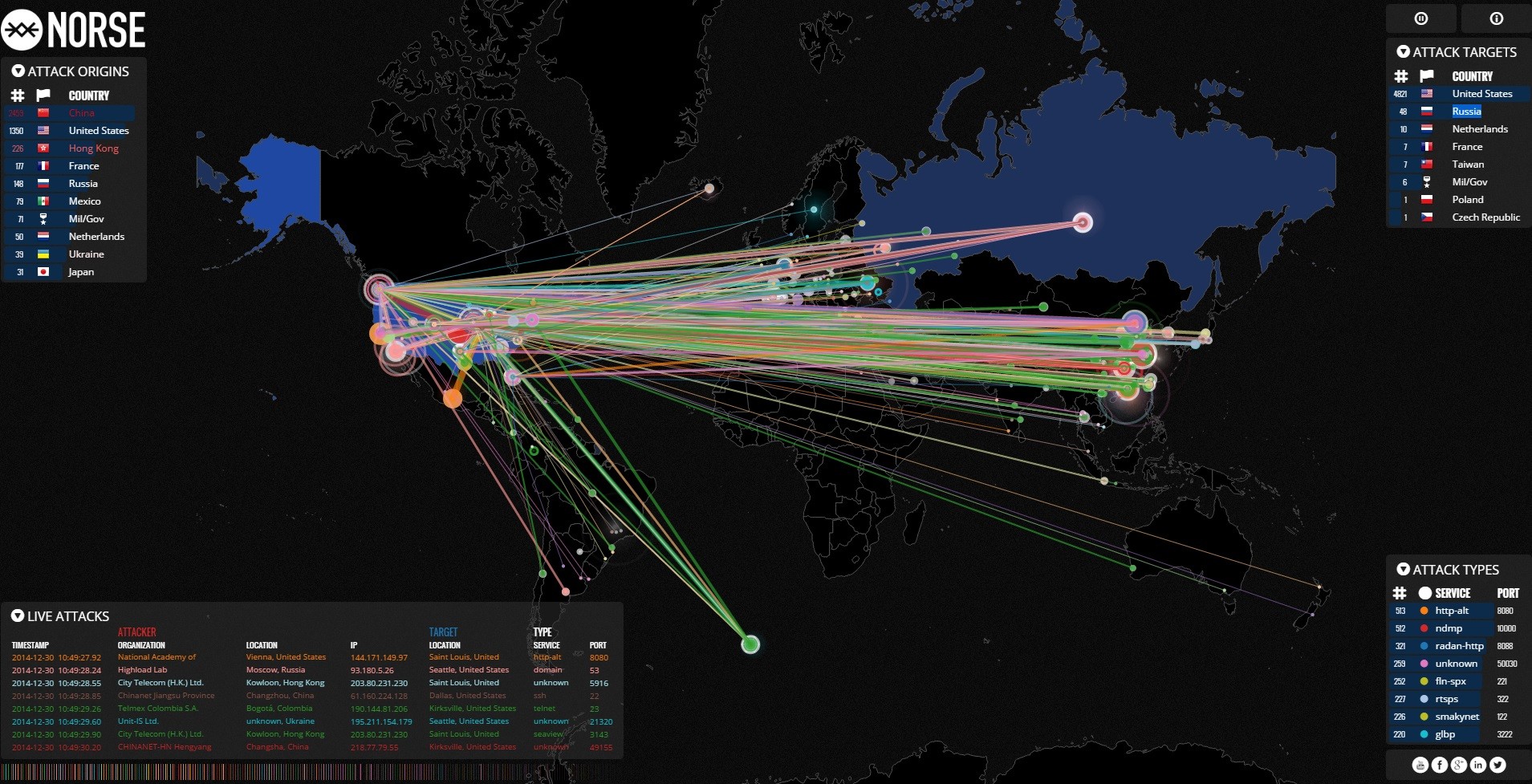
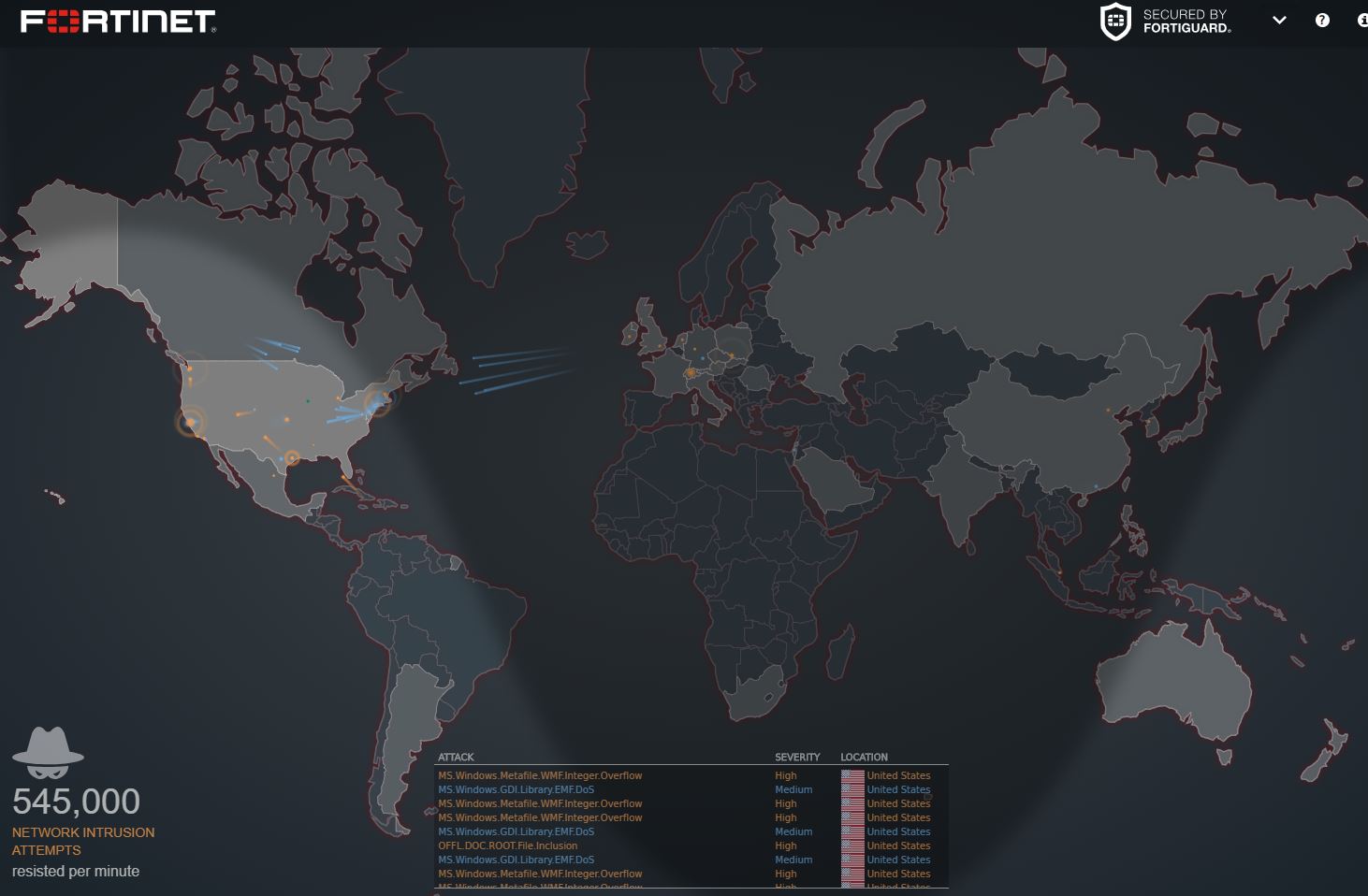
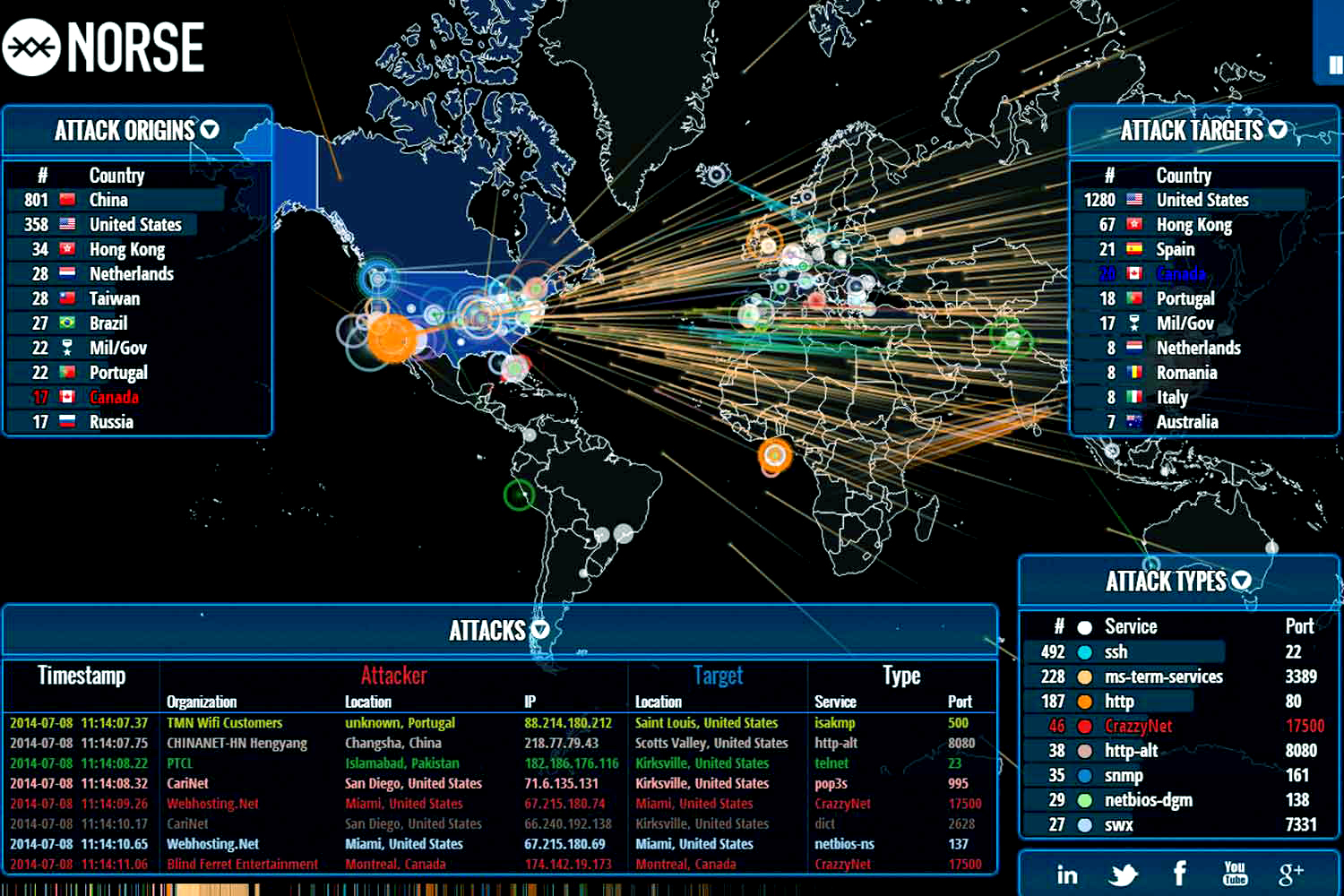
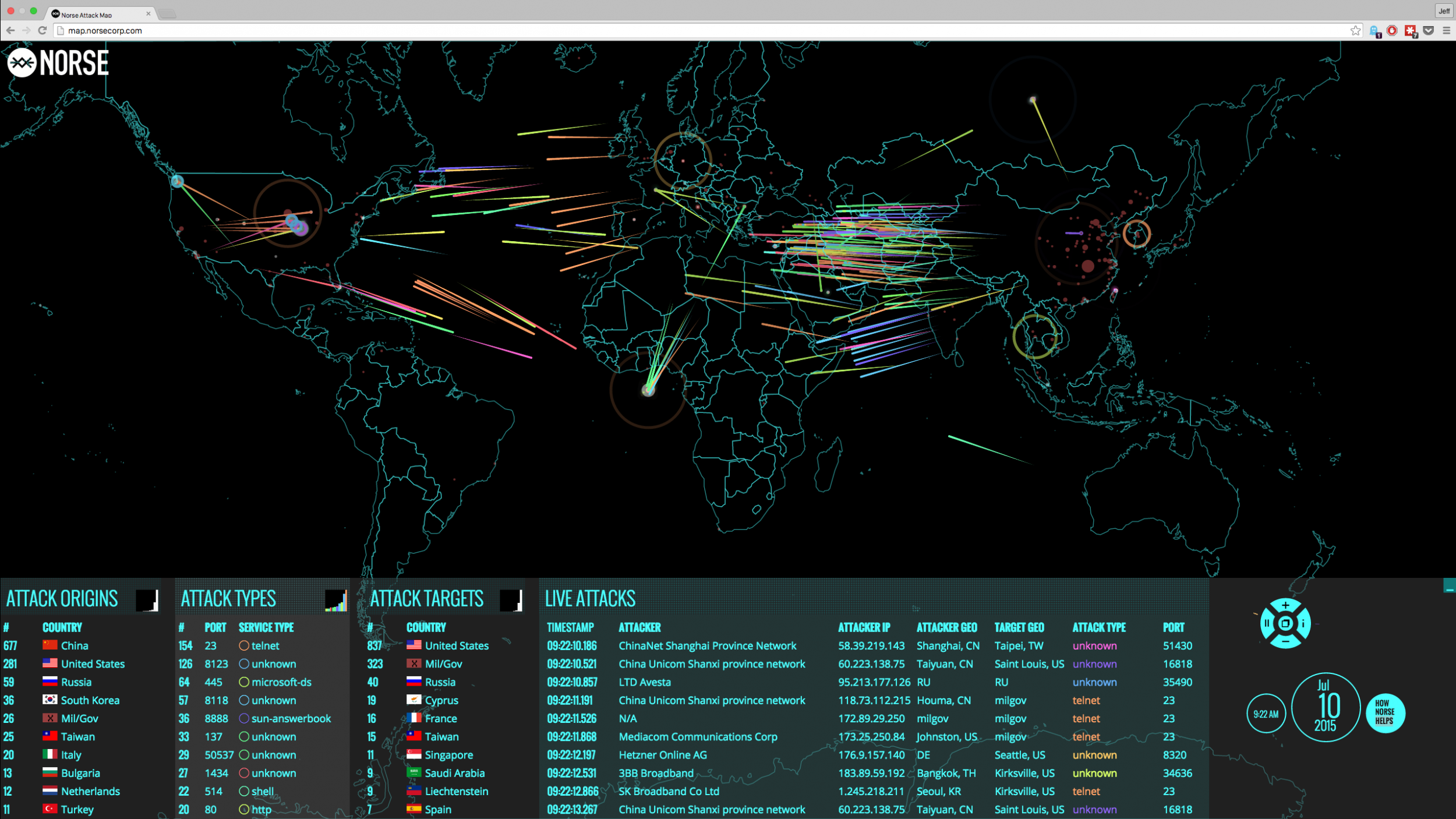
Cyber Attack Map - Norse Live Attack Map 3 22 00 Wireless Heat Maps Cybersecurity - 400wCybersecurity Supply And Demand - Dd9cc55a2fe4d8b16841187f793f74db ELEV8IT Tech Details - Zj8lpbpac801wgmqonr2Top 10 Cyber Attack Maps to See - Top Cyber Attack Maps Top 10 Security Project Risk Analysis - Risk Management Dashboard For Information Security Cybersecurity Risk Analysis And Management Plan Slide02 Vcom Technologies Tech Details - Gqzqs6rhobat8stzzyneNucleon Security Tech Details - D3w63oz3hjw5ajyticaw
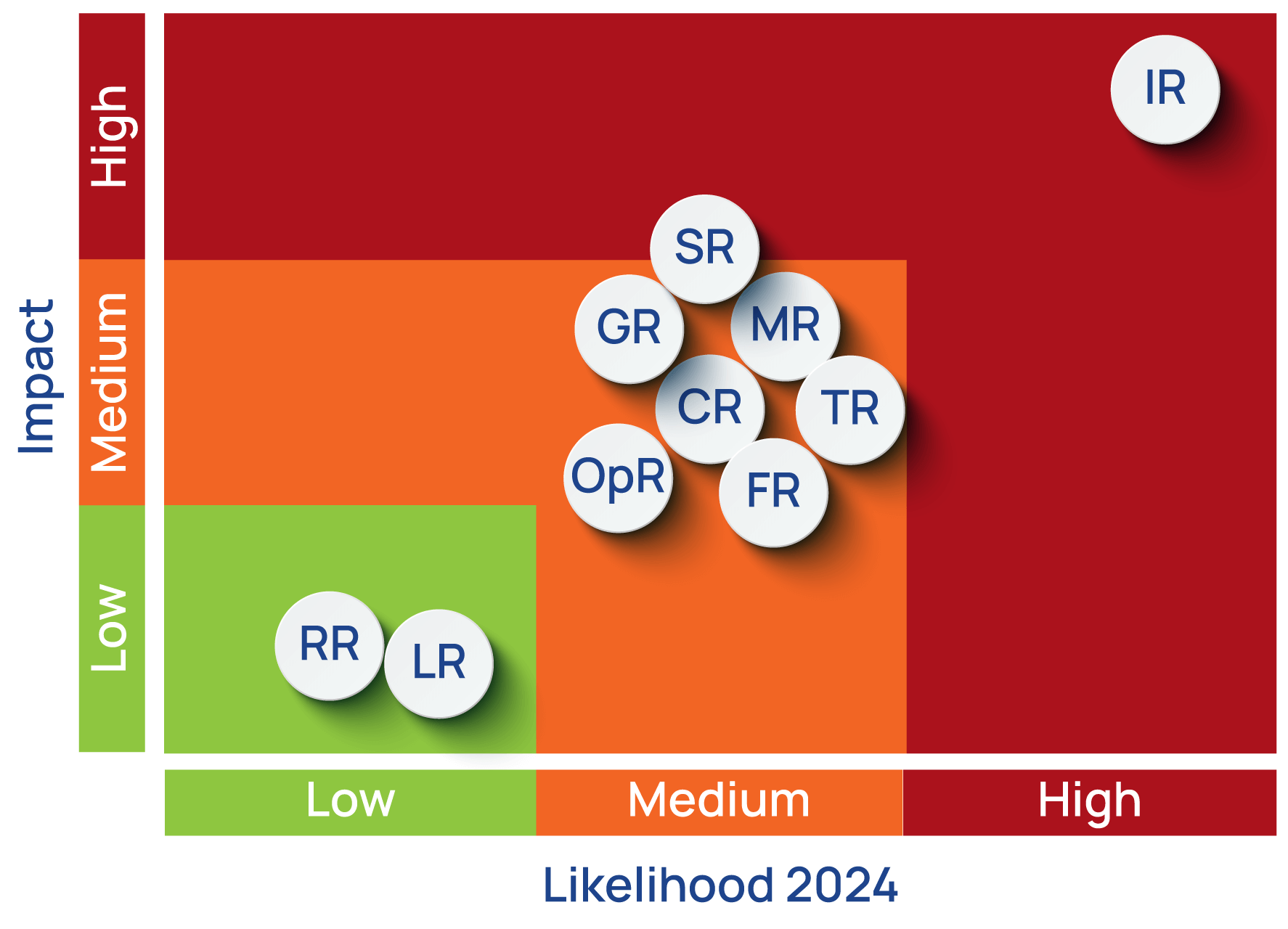
Cyber Risk Quantification GuidePoint - Dark Web Search And Monitoring Elementor Lt Real Time Cyber Threat Maps YouTube - Maxresdefault Why Cyber Risk Needs Numbers - 1744371965738Cisco Talos found MFA bypass techniques - 1752757332697Why Your Business Needs a Security - Cyber Security Heat Map Cybersecurity Digital Marketing - Profile.webpMain areas of security - Cybersecurity Map 1.0 Use Risk Visualization Tools to - Centric Consulting Risk Visualization Tools 2
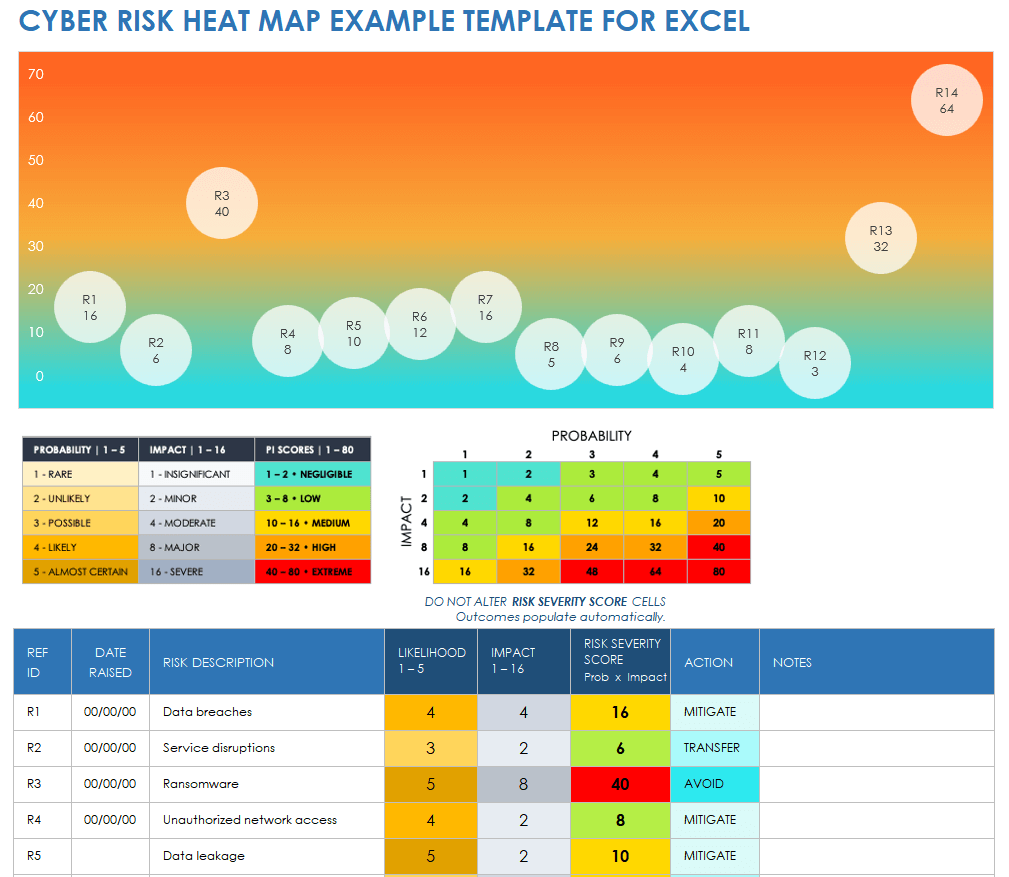
Risk Heat Map A Powerful Visualization - Risk Hear Map Powerful Tool E1553538402490 1 The Ultimate Guide To Cyber Threat - Cyberattackmap 1024x683 Free Risk Heat Map Templates - IC Cyber Risk Heat Map Example Template Heat Map Template for PowerPoint - Heat Map Template For PowerPoint Jpg Webp.webp